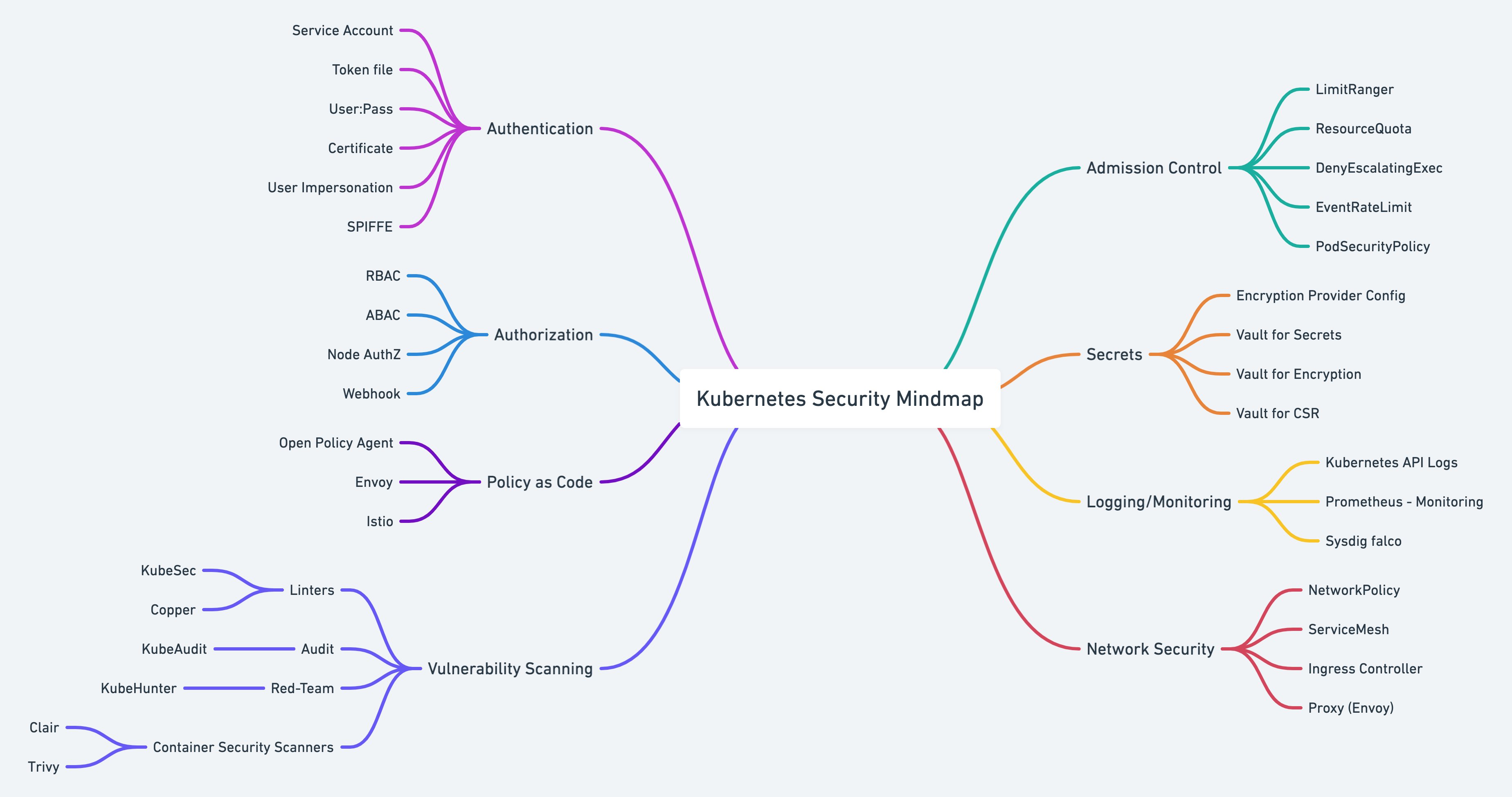
Kubernetes Security
- Introduction
- IAM Identity And Access Management in Kubernetes
- Securing Kubernetes Deployments
- Securing a Kubernetes cluster using TLS certificates. Wildcard certificates
- Kubernetes Security Scanners
- Security Checklist Kubernetes OWASP
- Exposed Kubernetes Clusters
- NSA National Security Agent Kubernetes Hardening Guidance
- CIS Benchmarks and CIS Operator
- User and Workload identities in Kubernetes
- Service Accounts
- Kubernetes Secrets
- Kubernetes Cert-Manager. Encrypting the certificate for Kubernetes. SSL certificates with Let’s Encrypt in Kubernetes Ingress via cert-manager
- Kubernetes OpenID Connect OIDC
- RBAC and Access Control
- Kubernetes and LDAP
- Admission Control
- Kubernetes Security Best Practices
- Kubernetes Authentication and Authorization
- Pod Security Policies (SCCs - Security Context Constraints in OpenShift)
- Security Profiles Operator
- EKS Security
- External Secrets Operator
- CVE
- Videos
- Tweets
Introduction
- cilium.io
- Dzone - devops security at scale
- Dzone - Kubernetes Policy Management with Kyverno
- Dzone - OAuth 2.0
- Kubernetes Security Best Practices 🌟
- jeffgeerling.com: Everyone might be a cluster-admin in your Kubernetes cluster
- Microsoft.com: Attack matrix for Kubernetes 🌟
- codeburst.io: 7 Kubernetes Security Best Practices You Must Follow
- thenewstack.io: Laying the Groundwork for Kubernetes Security, Across Workloads, Pods and Users
- horovits.wordpress.com: Kubernetes Security Best Practices
- containerjournal.com: How to Secure Your Kubernetes Cluster 🌟
- medium: How to Harden Your Kubernetes Cluster for Production 🌟
- kubernetes.io: Cloud native security for your clusters
- tldrsec.com: Risk8s Business: Risk Analysis of Kubernetes Clusters 🌟 A zero-to-hero guide for assessing the security risk of your Kubernetes cluster and hardening it.
- microsoft.com: Threat matrix for Kubernetes 🌟
- labs.bishopfox.com: Bad Pods: Kubernetes Pod Privilege Escalation 🌟 What are the risks associated with overly permissive pod creation in Kubernetes? The answer varies based on which of the host’s namespaces and security contexts are allowed. In this post, I will describe eight insecure pod configurations and the corresponding methods to perform privilege escalation. This article and the accompanying repository were created to help penetration testers and administrators better understand common misconfiguration scenarios.
- sysdig.com: Kubernetes Security Guide 🌟 Best practices, guidance and steps for implementing Kubernetes security.
- resources.whitesourcesoftware.com: Kubernetes Security Best Practices 🌟
- sysdig.com: Getting started with Kubernetes audit logs and Falco 🌟
- thenewstack.io: Best Practices for Securely Setting up a Kubernetes Cluster
- stackrox/Kubernetes_Security_Specialist_Study_Guide 🌟
- thenewstack.io: A Security Comparison of Docker, CRI-O and Containerd 🌟
- github.com/stackrox: Certified Kubernetes Security Specialist Study Guide 🌟
- youtube: Kubernetes Security: Attacking and Defending K8s Clusters - by Magno Logan
- cncf.io: Kubernetes Security 🌟
- microsoft.com: Secure containerized environments with updated threat matrix for Kubernetes
- kyverno.io 🌟 Kubernetes Native Policy Management. Open Policy Agent? That’s old school. Securely manage workloads on your kubernetesio clusters with this handy new tool, Kyverno.Kyverno is a policy engine designed for Kubernetes. With Kyverno, policies are managed as Kubernetes resources and no new language is required to write policies. This allows using familiar tools such as kubectl, git, and kustomize to manage policies. Kyverno policies can validate, mutate, and generate Kubernetes resources. The Kyverno CLI can be used to test policies and validate resources as part of a CI/CD pipeline. youtube: The Way of the Future | Kubernetes Policy Management with Kyverno - youtube: Securing and Automating Kubernetes with Kyverno
- kyverno.io/policies 🌟 K8s policies available in the community repository
- cyberark.com: Attacking Kubernetes Clusters Through Your Network Plumbing: Part 1
- redkubes.com: 10 Kubernetes Security Risks & Best Practices
- thenewstack.io: Defend the Core: Kubernetes Security at Every Layer
- Analyze Kubernetes Audit logs using Falco 🌟 Detect intrusions that happened in your Kubernetes cluster through audit logs using Falco
- blog.kasten.io: Kubernetes Ransomware Protection with Kasten K10 v4.0
- helpnetsecurity.com: Kubestriker: A security auditing tool for Kubernetes clusters 🌟 Kubestriker is an open-source, platform-agnostic tool for identifying security misconfigurations in Kubernetes clusters.
- Kubernetes Goat 🌟 is designed to be an intentionally vulnerable cluster environment to learn and practice Kubernetes security.
- itnext.io: How-To: Kubernetes Cluster Network Security 🌟
- gist.github.com: How to protect your ~/.kube/ configuration
- levelup.gitconnected.com: Enforce Audit Policy in Kubernetes (k8s)
- snyk.io: 10 Kubernetes Security Context settings you should understand
- magalix.com: Top 8 Kubernetes Security Best Practices 🌟
- redhat.com: The State of Kubernetes Security
- igorzhivilo.com: Network policy and Calico CNI to Secure a Kubernetes cluster
- fairwinds.com: Discover the Top 5 Kubernetes Security Mistakes You’re (Probably) Making
- tigera.io: Kubernetes security policy design: 10 critical best practices 🌟
- empresas.blogthinkbig.com: Descubierta una vulnerabilidad en Kubernetes que permite acceso a redes restringidas (CVE-2020-8562)
- thenewstack.io: Kubernetes: An Examination of Major Attacks 🌟 Constant vigilance is required to ensure that cloud infrastructure is locked down and that DevSecOps teams have the right tools for the job.
- cloud.redhat.com: Top Open Source Kubernetes Security Tools of 2021 🌟🌟
- cncf.io: How to secure your Kubernetes control plane and node components
- redhat.com: State of Kubernetes Security Report - Spring 2021 (PDF) 🌟
- kubernetes.io: Overview of Cloud Native Security 🌟🌟 This overview defines a model for thinking about Kubernetes security in the context of Cloud Native security.
- elastisys.com: NSA and CISA Kubernetes Security Guidance: Summarized and Explained
- learn.hashicorp.com: Integrate a Kubernetes Cluster with an External Vault 🌟
- talkingquickly.co.uk: Kubernetes Single Sign On - A detailed guide 🌟
- armosec.io: A Practical Guide to the Different Compliance Kubernetes Security Frameworks and How They Fit Together 🌟🌟
- thenewstack.io: How to Secure Kubernetes, the OS of the Cloud
- akhilsharma.work: The 4C’s of Kubernetes Security
- Kubernetes security thing: Always be careful of what you are letting your users choose for usernames. If someone has a username of system:kube-controller-manager on an external Identity system, Kubernetes will quite happily give them the rights of the controller manager. The –oidc-username-prefix and –oidc-groups-prefix flags are userful for preventing this in OIDC integrations.
- medium: Securing the Kubernetes cluster | Lessandro Z. Ugulino
- infoworld.com: The race to secure Kubernetes at run time A new wave of startups is looking to help developers secure their containerized applications after they go into production. Is this the future of application security?
- goteleport.com: Kubernetes API Access Security Hardening
- infoworld.com: Securing the Kubernetes software supply chain with Microsoft’s Ratify Microsoft’s Ratify proposal adds a verification workflow to Kubernetes container deployment. The Ratify team has some demo code in their GitHub repository that shows how to use Ratify with Gatekeeper in Kubernetes. Ratify installs using a Helm chart, bringing along some sample configuration templates.
- amazicworld.com: Top 5 security threats unique to a Kubernetes and Cloud Native stack
- peoplactive.com: Kubernetes and Container Security Checklist to Build Secure Apps
- venturebeat.com: Kubernetes security will have a breakout year in 2022
- medium: Comparing Kubernetes Security Frameworks and Guidance 🌟 Comparing popular Kubernetes security and compliance frameworks, how they differ, when to use, common goals, and suggested tools.
- blog.gitguardian.com: Hardening Your Kubernetes Cluster - Threat Model (Pt. 1) 🌟 The NSA and CISA recently released a guide on Kubernetes hardening. We’ll cover this guide in a three part series. First, let’s explore the Threat Model and how it maps to K8s components.
- blog.gitguardian.com: Hardening Your Kubernetes Cluster - Guidelines (Pt. 2) 🌟 In this second episode, we will go through the NSA/CISA security recommendations and explain every piece of the guidelines.
- blog.devgenius.io: How is security managed in Kubernetes clusters? Best practices for managing security in Kubernetes at various layers
- blog.gitguardian.com: Kubernetes Hardening Tutorial Part 1: Pods Get a deeper understanding of Kubernetes Pods security with this first tutorial. After reading this article, you will learn:
- How not to run pods as root
- How to use immutable root fs (lock the root filesystem)
- How to do Docker image scan locally and with your CI pipelines
- How to use PSP
- blog.gitguardian.com: Kubernetes Hardening Tutorial Part 2: Network How to achieve Control Plane security, true resource separation with network policies, and use Kubernetes Secrets more securely.
- infoworld.com: 10 steps to automating security in Kubernetes pipelines DevOps teams don’t need to sacrifice the speed of containerized development if they know what can be automated, why it’s important, and how to do it
- medium.com/@jonathan_37674: Kubernetes Security Best Practices: Definitive Guide
- isovalent.com: Detecting a Container Escape with Cilium and eBPF In this article you’ll learn how an attacker with access to a Kubernetes cluster can escape from a container and:
- run a pod to gain root privileges
- escape to the host
- persist the attack with invisible pods and fileless executions
- mattermost.com: The Top 7 Open Source Tools for Securing Your Kubernetes Cluster
- infoworld.com: 10 steps to automating security in Kubernetes pipelines DevOps teams don’t need to sacrifice the speed of containerized development if they know what can be automated, why it’s important, and how to do it.
- developers.redhat.com: Secure your Kubernetes deployments with eBPF Learn how to use eBPF and the Security Profiles Operator to automatically generate seccomp profiles, a Linux kernel security feature for Kubernetes
- tutorialboy24.medium.com: A Detailed Brief About Offence and Defence on Cloud Security — Etcd Risks In this article, you will explore several scenarios on how to attack etcd in Kubernetes to gain access to its data. You will cover:
- Etcd localhost port access due to SSRF vulnerability
- Etcd Credential Stealing
- Kube API server command execution
- faun.pub: From dev to admin: an easy Kubernetes privilege escalation you should be aware of — the attack In this post, you will learn how easily a limited user (such as a developer) can escalate their privileges and become an admin of a cluster which has been set up using kubeadm.
- xenitab.github.io: Kubernetes Ephemeral Container Security 🌟 Ephemeral containers are temp containers that can be attached after a Pod is created. But what happens when you use them on a hardened cluster? The answer is not so obvious as OPA, Kyverno, PSPs, etc. will do their best to (rightly) prevent execution.
- armosec.io: How to Secure Deployments in Kubernetes? 🌟 In Kubernetes, there are two aspects to security: cluster security and application security. In this post, you’ll explore how to secure Kubernetes deployments and applications in general.
- medium.com/@dotdc: Is your Kubernetes API Server exposed? Learn how to check and fix! 🌟
- elastisys.com: Why and how should you reboot Kubernetes Nodes? 🌟 Regularly rebooting Kubernetes Nodes is necessary for a healthy security posture. In this article, you will learn how you can reboot your Nodes securely, when and how to avoid common mistakes that could cause downtime (i.e. PodDisruptionBugdets)
- levelup.gitconnected.com: The Core of Kubernetes Security: Clusters
- sysdig.com: How attackers use exposed Prometheus server to exploit Kubernetes clusters | Miguel Hernández What happens if an attacker accesses your Prometheus server? How much information can they get for fingerprinting the cluster? In this article, you will learn how attackers use this information and how to secure your cluster.
- cast.ai: Kubernetes Security: 10 Best Practices from the Industry and Community 🌟
- thenewstack.io: Basic Principles Key to Securing Kubernetes’ Future Once these capabilities have been established, Ops teams can begin to look further afield and explore leveraging the value of their data through activities like testing and optimization.
- medium.com/@codingkarma: Kubernetes Goat Part-1 In this article, you will learn how to attack and defend a Kubernetes cluster by solving the challenges of Kubernetes goat — an intentionally vulnerable cluster environment to learn and practice Kubernetes security
- medium.com/@badawekoo: Limit number of processes running in a Kubernetes pod When it comes to Kubernetes security, It is very important to harden the core components of the cluster which are pods, and limit the risks that can be originated from inside the pods. That’s why limiting number of processes that can run inside a pod will limit any vulnerabilities in your cluster.
- copado.com: Applying a Zero Trust Infrastructure in Kubernetes
- dev.to/pavanbelagatti: Kubernetes Security Best Practices For Developers
- itnext.io: Journey Of A Microservice Application In The Kubernetes World 🌟 Security considerations: security related tools. In this article, you will discuss some security considerations and see how you can ensure (at least to some extent) that the application’s specifications follow some of the best security practices.
- tutorialboy24.blogspot.com: A Detailed Talk about K8S Cluster Security from the Perspective of Attackers (Part 2) 🌟 In this 2-part series, you will address 12 common attack points in Kubernetes clusters and discuss various risks in cloud-native scenarios based on practical experience
- medium.com/cloudyrion: Kubernetes end-to-end chain exploit This article details the security flaws discovered in Kubernetes and GitOps tools due to improper configurations. It also demonstrates how an attacker could perform post-exploitation attacks, increasing their privileges and the attack surface.
- itnext.io: Performing Security Checks for Deployed Kubernetes Manifests An effective tool for checking security rule violations in Kubernetes deployments using Polaris
- securitycafe.ro: A COMPLETE KUBERNETES CONFIG REVIEW METHODOLOGY
- itnext.io: Introduction to Kubernetes Security for Security Professionals Presenting the architecture of Kubernetes and its associated security threats, for security professionals, including penetration testers and DevSecOps practitioners.
- dev.to/mattiasfjellstrom: Kubernetes-101: Security concepts The article provides an overview of Kubernetes security concepts, focusing on NetworkPolicies, ServiceAccounts, and Security Contexts
- blog.alexellis.io: What if your Pods need to trust self-signed certificates? Self-signed certificates are common within enterprise companies. But how do you distribute them and enable their use in Kubernetes as a user and a vendor?
- thenewstack.io: Securing Kubernetes in a Cloud Native World As cloud native technologies continue to advance, staying informed and adaptable is key to maintaining a secure Kubernetes ecosystem.
- collabnix.com: Applying DevSecOps Practices to Kubernetes
- dev.to/thenjdevopsguy: Securing Kubernetes Pods For Production Workloads
- dev.to/thenjdevopsguy: The 4 C’s Of Kubernetes Security
IAM Identity And Access Management in Kubernetes
- thenewstack.io: Cloud Native Identity and Access Management in Kubernetes
- curity.io: OAuth 2.0 Overview
- curity.io: OpenID Connect Overview
- curity.io: Client Security Client security primarily covers web and mobile, to ensure best security in the browser and on devices
- dev.to/gabrielbiasi: Automatic SSO in Kubernetes workloads using a sidecar container In this tutorial, you will learn how to use oauth2-proxy as a sidecar container to authorize requests to your Identity Provider of choice
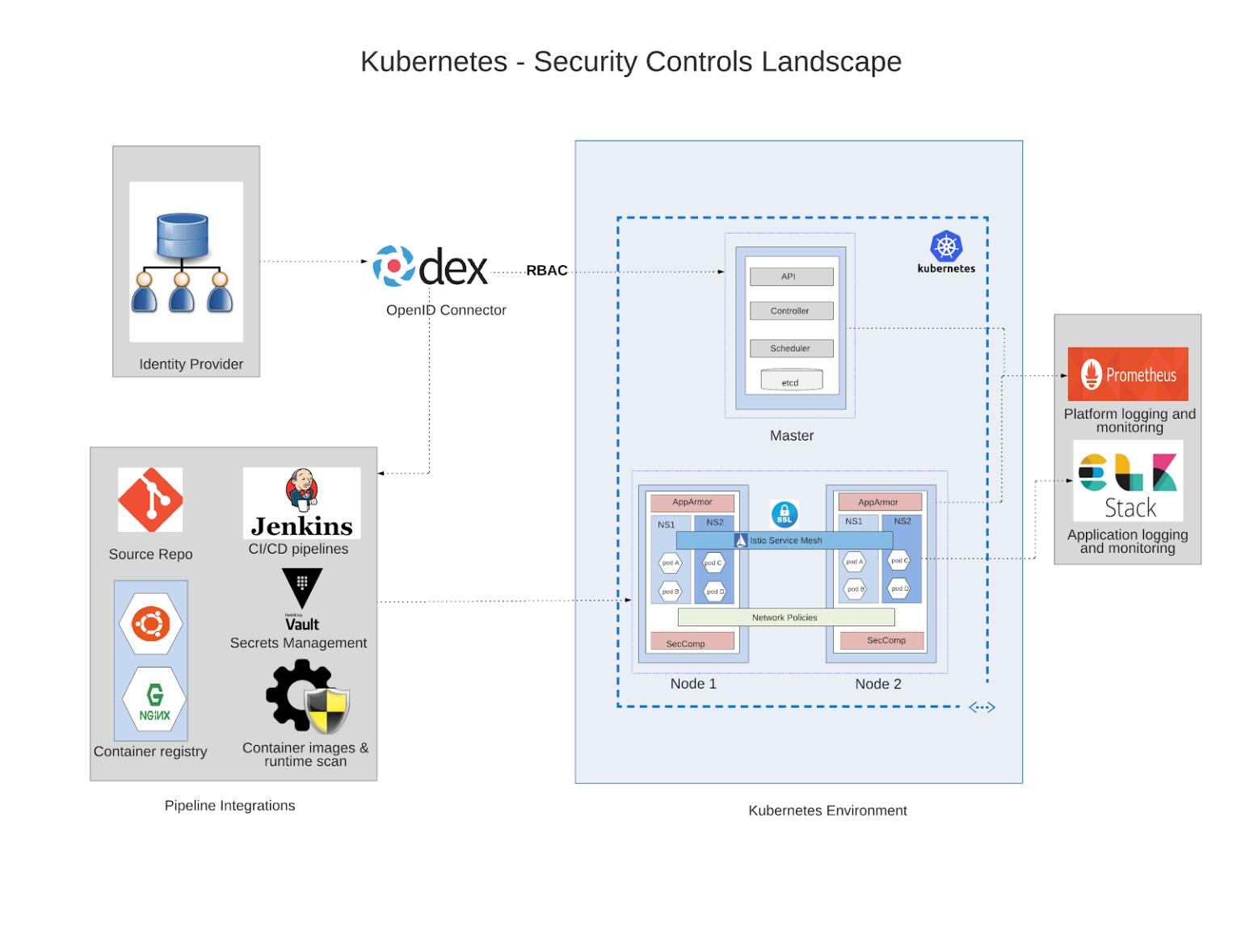
Securing Kubernetes Deployments
- dev.to/aws-builders: Best Practices for Securing Kubernetes Deployments 🌟 Although Kubernetes is a powerful container orchestration platform, its complexity and its adoption makes it a prime target for security attacks. We’ll go over some of the best practices for securing the Kubernetes deployments and keeping applications and data safe in this article. This article is only about pods or deployments.
Securing a Kubernetes cluster using TLS certificates. Wildcard certificates
- thenewstack.io: Jetstack Secure Promises to Ease Kubernetes TLS Security
- xgrid.medium.com: Securing a Kubernetes cluster using TLS certificates 🌟
- ahmedy.hashnode.dev: Creating TLS Certificates for K8s components with OpenSSL In this guide, you will discuss how to create key/certificate pairs using OpenSSL to facilitate secure communication between Kubernetes Cluster components
- erkanzileli.medium.com: How TLS Certificates Work
- medium.com/@martin.hodges: Using a wildcard certificate within your Kubernetes cluster
Kubernetes Security Scanners
- blog.cloudsecque.com: How to Improve the Security of Your Applications with Kubernetes Security Scanners Kubernetes security scanners are tools that can be used to detect vulnerabilities and security issues in your applications. In this article you will find:
- Grype
- Trivy
- Kubesec
- Kube-bench
- Kubeaudit
- techmanyu.com: Kubernetes Security with Kube-bench and Kube-hunter 🌟
- kube-bench 🌟 Checks whether Kubernetes is deployed according to security best practices as defined in the CIS Kubernetes Benchmark
- kube-hunter 🌟 Hunt for security weaknesses in Kubernetes clusters
- k21academy.com: Secure and Harden Kubernetes, AKS and EKS Cluster with kube-bench, kube-hunter and CIS Benchmarks 🌟
- aninditabasak.medium.com: A Lap around Kubernetes Security & Vulnerability scanning Tools — checkov, kube-hunter, kube-bench & Starboard
- towardsdatascience.com: How to Secure your Kubernetes Deployment 🌟 It takes 20 years to build a reputation and few minutes of cyber-incident to ruin it. — Stephane Nappo. Kubernetes deployments are not safe by default and you should go the extra mile and secure the gates. Fortunately, tools like kube-bench let us focus our attention on specific areas of the cluster.
- blog.flant.com: Kubernetes cluster security assessment with kube-bench and kube-hunter
- raesene.github.io: Let’s talk about Kubernetes on the Internet In this article, you will learn how to scan and discover publicly accessible Kubernetes clusters and how you can protect against it
- github.com/Shopify/kubeaudit 🌟🌟 kubeaudit helps you audit your Kubernetes clusters against common security controls. kubeaudit is a command line tool and a Go package to audit Kubernetes clusters for various different security concerns, such as:
- Run as non-root
- Use a read-only root filesystem
- Drop scary capabilities, don’t add new ones
- Don’t run privileged
- towardsdev.com: 12 Scanners to Find Security Vulnerabilities and Misconfigurations in Kubernetes
Security Checklist Kubernetes OWASP
- kubernetes.io: Security Checklist 🌟🌟
- itnext.io: Kubernetes OWASP Top 10: Centralised Policy Enforcement This article covers the techniques for centralised policy enforcement in a Kubernetes cluster:
- CI/CD pipelines
- Security Admission controller
- OPA and Gatekeeper
- IDE linting and plug-ins
- faun.pub: Gatekeeper | K8 hardening backlog This article summarizes a list of recommendations for hardening Kubernetes clusters (both on-prem and cloud) with Admission and Mutation webhooks using the open-source tool Gatekeeper.
- systemweakness.com: OWASP-K8S Security: Insecure Workload Configurations In this series of blogs we will focus on OWASP Top 10 Kubernetes vulnerabilities, Discussing each in a separate blog.
- owasp.org: OWASP Kubernetes Top Ten OWASP Kubernetes Top Ten is aimed at helping security practitioners, system administrators, and developers prioritize risks around the Kubernetes ecosystem. This is a prioritized list of these risks backed by data.
- darkreading.com: Top 10 Kubernetes Security Risks Every DevSecOps Pro Should Know The mission to run any containerized application on any infrastructure makes security a challenge on Kubernetes.
- sysdig.com: OWASP Kubernetes Top 10 🌟 One of the biggest concerns when using Kubernetes is whether we are complying with the security posture and taking into account all possible threats.
- itnext.io: Kubernetes OWASP Top 10: Secrets Management In this article, you will discuss secrets management in Kubernetes:
- Secrets objects
- Managing Kubernetes Secrets
- Manual Secret Creation
- Secrets in CI/CD pipelines
- Kubernetes Secrets Store Container Storage Interface
Exposed Kubernetes Clusters
- blog.cyble.com: Exposed Kubernetes Clusters Organizations At Risk Of Data Breaches Via Misconfigured Kubernetes. Over 900k Kubernetes exposures were observed across the internet during a routine threat-hunting exercise. While this does not imply that all exposed instances are vulnerable to attacks, it still makes them a target.
NSA National Security Agent Kubernetes Hardening Guidance
- nsa.gov: NSA, CISA release Kubernetes Hardening Guidance 🌟🌟
- Kubernetes Hardening Guidance 🌟🌟
- thenewstack.io: The NSA Can Help Secure Your Kubernetes Clusters
- therecord.media: NSA, CISA publish Kubernetes hardening guide 🌟🌟
- Scan containers and Pods for vulnerabilities or misconfigurations.
- Run containers and Pods with the least privileges possible.
- Use network separation to control the amount of damage a compromise can cause.
- Use firewalls to limit unneeded network connectivity and encryption to protect confidentiality.
- Use strong authentication and authorization to limit user and administrator access as well as to limit the attack surface.
- Use log auditing so that administrators can monitor activity and be alerted to potential malicious activity.
- Periodically review all Kubernetes settings and use vulnerability scans to help ensure risks are appropriately accounted for and security patches are applied.
- cloud.redhat.com: OpenShift and the NSA-CISA ‘Kubernetes Hardening Guidance’ Red Hat OpenShift is the quickest path to meeting the NSA’s Kubernetes hardening guidance
- Kubescape 🌟 kubescape is the first tool for testing if Kubernetes is deployed securely as defined inKubernetes Hardening Guidance by to NSA and CISA. Tests are configured with YAML files, making this tool easy to update as test specifications evolve.
- infoq.com NSA and CISA Publish Kubernetes Hardening Guidance
- csoonline.com: Kubernetes hardening: Drilling down on the NSA/CISA guidance The new guidance gives a solid foundation for hardening Kubernetes container environments.These are its key components and why they are important.
- armosec.io: Kubescape - As “left” as it can get – find Kubernetes security issues while coding, not after
- theregister.com: Hardening Kubernetes the NSA way. NSA spies ample opportunities to harden Kubernetes
- thenewstack.io: NSA on How to Harden Kubernetes
- blog.gitguardian.com: Hardening Your Kubernetes Cluster - Threat Model (Pt. 1) 🌟🌟 The NSA and CISA recently released a guide on Kubernetes hardening. We’ll cover this guide in a three part series. First, let’s explore the Threat Model and how it maps to K8s components.
- blog.gitguardian.com: Hardening Your Kubernetes Cluster - Guidelines (Pt. 2) In this second episode, we will go through the NSA/CISA security recommendations and explain every piece of the guidelines.
- blog.gitguardian.com: Kubernetes Hardening Tutorial Part 1: Pods Get a deeper understanding of Kubernetes Pods security with this first tutorial.
- blog.gitguardian.com: Kubernetes Hardening Tutorial Part 2: Network How to achieve Control Plane security, true resource separation with network policies, and use Kubernetes Secrets more securely.
- blog.gitguardian.com: Kubernetes Hardening Tutorial Part 3: Authn, Authz, Logging & Auditing In this tutorial, you will learn the authentication, authorization, logging, and auditing of a Kubernetes cluster. Specifically, you will discuss some of the best practices in AWS EKS.
- armosec.io: NSA & CISA Kubernetes Hardening Guide – what is new with version 1.1 In March 2022, NSA & CISA has issued a new version of the Kubernetes Hardening Guide – 1.1. Here are the most important points addressed in this new version.
- elastisys.com: Free Guide: How to security harden Kubernetes in 2022 Kubernetes is neither secure by default, nor by itself. You absolutely can, and must, harden its configuration. This article summarises the NSA/CISA guidelines on security hardening Kubernetes.
CIS Benchmarks and CIS Operator
- ibm.com: CIS Benchmarks Developed by a global community of cybersecurity professionals, CIS Benchmarks are a collection of best practices for securely configuring IT systems, software, networks, and cloud infrastructure.
- aymen-abdelwahed.medium.com: K8s Operators — CIS Kubernetes Benchmarks How can I run my workloads securely on top of Kubernetes? In this post, we’ll be taking a look at the CIS-Benchmark, breaking the concept down to simple terms, and in the end, deploying the CIS-Operator using Helm charts and custom values
- rancher/cis-operator This is an operator that can run on a given Kubernetes cluster and provide ability to run security scans as per the CIS benchmarks, on the cluster.
User and Workload identities in Kubernetes
- learnk8s.io/authentication-kubernetes: User and workload identities in Kubernetes 🌟🌟🌟
- The difference b/w externally managed and internal identities.
- How Kubernetes assigns identities for internal users with Service Accounts.
Service Accounts
- Service account is an important concept in terms of Kubernetes security. You can relate it to AWS instance roles and google cloud instance service account if you have a cloud background. By default, every pod gets assigned a default service account if you don’t specify a custom service account. Service account allows pods to make calls to the API server to manage the cluster resources using ClusterRoles or resources scoped to a namespace using Roles. Also, you can use the Service account token from external applications to make API calls to the kubernetes API server.
- devopscube.com: How To Create Kubernetes Service Account For API Access
- devopscube.com: How to Create kubernetes Role for Service Account
- github.com/scriptcamp/kubernetes-serviceaccount-example Example Kubernetes manifests to create service account mapped to Rolebinding.
- medium: Working with Service Account In Kubernetes 🌟 How to configure a service account in Kubernetes and manage it?
- github.com/dvob/k8s-s2s-auth: Kubernetes Service Accounts 🌟 Service accounts are well known in Kubernetes to access the Kubernets API from within the cluster. This is often used for infrastructure components like operators and controllers. But we can also use service accounts to implement authentication in our own applications. This README tries to give an overview on how service accounts work and and shows a couple of variants how you can use them for authentication. Further this repository contains an example Go service which shows how to implement the authentication in an application.
- sandeepbaldawa.medium.com: Service Accounts in K8s (Kubernetes)
- mjarosie.github.io: IAM roles for Kubernetes service accounts - deep dive
- linkerd.io: Using Kubernetes’s new Bound Service Account Tokens for secure workload identity
- medium.com/pareture: Kubernetes Bound Projected Service Account Token Volumes Might Surprise You There is an important difference to understand and remember between default Service Account Projection and Bound Service Account Token Volumes.
- medium.com/geekculture: K8s — ServiceAccount Token K8s ServiceAccount token deep dive
- motilayo.hashnode.dev: Exploring Kubernetes Service Account Tokens and Secure Workload Identity Federation Ever wonder how AWS IRSA, GCP workload identity or Azure AD workload identity work in Kubernetes? This article explores how OIDC works in a Kubernetes cluster to trust external workloads
- overcast.blog: Kubernetes Service Accounts: A Practical Guide
Kubernetes Secrets
- cncf.io: Revealing the secrets of Kubernetes secrets 🌟 In this article you will learn how to protect Secrets in your Kubernetes cluster
- Hands on your first Kubernetes secrets 🌟
- dev.to: Store your Kubernetes Secrets in Git thanks to Kubeseal. Hello SealedSecret! 🌟
- blog.doit-intl.com: Kubernetes and Secrets Management in the Cloud
- itnext.io: Effective Secrets with Vault and Kubernetes
- kubernetes.io: Encrypting Secret Data at Rest 🌟
- “Kubernetes base64 encodes secrets because that makes arbitrary data play nice with JSON. It had nothing to do with the security model (or lack thereof). It did not occur to us at the time that people could mistake base64 for some form of encryption”
- “I’ve always wondered how folks expect a system would be able to protect data at rest like that. If the public key and private key are local on the machine - nothing is secure no matter what algorithm is used”
- “The issue is not new or unique to k8s. There is a general confusion between encoding and encryption. Ask any web dev about base64, and there is a good chance they’ll tell you it’s encryption”
- “The test is clearly wrong if that is the word used, literally everything is encoded somehow. If they meant encrypted instead, then it’s half true, secrets are encrypted in transit but only at rest if a KMS plugin is used”
- “The semantics are important. Easy to grant an RBAC policy like “read only except secrets”
- “I just meant that base64 prevents you from logging a secret in plain text by accident… but many more layers are required to keep your secrets secret”
- “You need to configure how the key is managed and ideally opt into something like KMS plugin (which depends on how the cluster is hosted) to make it good”
- redhat.com: Managing secrets for Kubernetes pods
- enterprisersproject.com: How to explain Kubernetes Secrets in plain English 🌟 What is a Kubernetes secret? How does this type of Kubernetes object increase security? How do you create a Kubernetes secret? What are some best practices? Experts break it down
- millionvisit.blogspot.com: Kubernetes for Developers #19: Manage app credentials using Kubernetes Secrets 🌟
- kubermatic.com: Keeping the State of Apps Part 2: Introduction to Secrets
- medium: Kubernetes Secrets Explained
- medium: Managing your sensitive information during GitOps process with Secret Sealed
- enlear.academy: Sealed Secrets with Kubernetes Usage of the sealed secret to encrypt Kubernetes secrets.
- medium.com/codex: Sealed Secrets for Kubernetes How to encrypt Kubernetes Secret component and store it on the Git. And decrypt it using Kubernetes controller.
- macchaffee.com: Plain Kubernetes Secrets are fine 🌟 It’s no secret that Kubernetes Secrets are just base64-encoded strings stored in etcd alongside the rest of the cluster’s state. But is it really an issue? Let’s create a rudimentary threat model for Kubernetes Secrets and see what comes up.
- youtube: Manage Kubernetes Secrets With External Secrets Operator (ESO) 🌟
- carlosalca.medium.com: How to manage all my K8s secrets in git securely with Bitnami Sealed Secrets
- cloud.redhat.com: A Guide to Secrets Management with GitOps and Kubernetes 🌟 This article will discuss two architectural approaches to managing secrets with GitOps: encrypted secrets stored in Git and storing a reference to secrets in Git
- itnext.io: Vault cluster with auto unseal on Kubernetes
- pjame-fb.medium.com: Kubernetes Secrets from Secrets Manager using External Secrets Operators In this article, you will learn how to store your credentials in the Secrets Manager and automatically retrieve them for creating Kubernetes Secrets using External Secrets.
- mixi-developers.mixi.co.jp: Comparing External Secrets Operator with Secret Storage CSI as Kubernetes External Secrets is Deprecated In this article, you will compare the External Secrets Operator with Secret Storage CSI for using external secrets in a Kubernetes cluster. You will compare:
- Architecture
- Authorization management
- Resource usage
- GitOps friendliness
- faun.pub: Secrets | Kubernetes A deep dive into Kubernetes Secrets
- medium.com/@knoldus: Using sealed secrets in Kubernetes
- eminalemdar.medium.com: Cloud Native Secret Management with External Secrets Operator
- piotrminkowski.com: Sealed Secrets on Kubernetes with ArgoCD and Terraform In this article, you will learn how to manage secrets securely on Kubernetes in the GitOps approach using Sealed Secrets, ArgoCD, and Terraform
- medium.com/google-cloud: Handle Kubernetes Secrets the GitOps Way — Part 1
- dev.to: A Detailed Talk about K8S Cluster Security from the Perspective of Attackers (Part 1) This 2-part series summarizes the methods and experience of attacking Kubernetes components, external services of nodes, business pods, and container escaping, including lateral attacks, as well as attacks on the Kubernetes management platform
Kubernetes Cert-Manager. Encrypting the certificate for Kubernetes. SSL certificates with Let’s Encrypt in Kubernetes Ingress via cert-manager
- cert-manager.io 🌟 cert-manager adds certificates and certificate issuers as resource types in Kubernetes clusters, and simplifies the process of obtaining, renewing and using those certificates. It can issue certificates from a variety of supported sources, including Let’s Encrypt, HashiCorp Vault, and Venafi as well as private PKI.
- Kubernetes Certs
- Using SSL certificates from Let’s Encrypt in your Kubernetes Ingress via cert-manager 🌟
- medium: Encrypting the certificate for Kubernetes (Let’s Encrypt) 🌟
- rejupillai.com: Let’s Encrypt the Web (for free)
- betterprogramming.pub: Kubernetes and SSL Certificate Management 🌟 Manage SSL certificate orders in K8s with Helm and Let’s Encrypt.
- getbetterdevops.io: How to Secure K8S Nginx Ingress With Let’s Encrypt and Cert Manager Automate the provisioning of Let’s Encrypt certificates for ingress resources
- faun.pub: Automate Certificate Management In Kubernetes Using Cert-Manager
- cert-manager/cert-manager Automatically provision and manage TLS certificates in Kubernetes
- github.com/cert-manager: Policy Approver Policy Approver is a cert-manager approver that is responsible for Approving or Denying CertificateRequests.
- jetstack.io: Getting started using cert-manager with the sig-network Gateway API
- medium.com/@knoldus: Configure SSL certificate with cert-manager on Kubernetes
- blog.devgenius.io: Automated DNS/TLS with External DNS & LetsEncrypt on Kubernetes In this article, you’ll learn how to create TLS certificates for your application with cert-manager and DNS entries with external DNS. Finally, you will expose your applications with an ingress resource to tie it all together.
- itnext.io: Upgrade Cert-Manager for Your Production Deployment Without Downtime When upgrading Cert-Manager, it’s often required to update the CRDs. Unfortunately, it’s not a straightforward process. In this article, you’ll learn a few options that ensure a smooth Cert-Manager upgrade to avoid downtime of production deployment.
- faun.pub: Let’s encrypt and CertManager How to use CertManager and Let’s encrypt in Kubernetes
- armin.su: SSL certificates from Let’s Encrypt for Kubernetes Private Ingress via Terraform
- dev.to: Kubernetes TLS, Demystified 🌟
Kubernetes OpenID Connect OIDC
- gini/dexter dexter is an OIDC (OpenId Connect) helper designed to create a hassle-free Kubernetes login experience powered by Google or Azure as Identity Provider. All you need is a properly configured Google or Azure client ID & secret
- betterprogramming.pub: Kubernetes Authentication Sidecars: A Revelation in Microservice Architecture A history of authentication and how to solve authentication in a reusable way using sidecar containers in Kubernetes
- blog.devgenius.io: SSO Authentication for Applications in Kubernetes This post discusses using SSO authentication and authorization to secure apps in Kubernetes. The tutorial uses Dex and Traefik Forward Auth (or Oauth2-Proxy) to add additional security to ingresses or apps that do not support built-in OIDC
OAuth2 Proxy
OAuth2 Proxy is an open-source reverse proxy that provides authentication and authorization for web applications. It is designed to sit in front of your web application and authenticate users using OAuth2 providers such as Google, Microsoft, and Facebook. Once a user has been authenticated, OAuth2 Proxy adds an authorization header to each request, allowing the web application to verify that the request came from an authenticated user.
OAuth2 Proxy is commonly used in Kubernetes environments to secure access to web applications deployed on a Kubernetes cluster. It integrates with Kubernetes API Server to provide automatic configuration and discovery of the OAuth2 provider’s credentials. It also supports a variety of authentication mechanisms, including Google OAuth2, Microsoft Azure AD, GitHub OAuth2, and others.
Some of the key features of OAuth2 Proxy include:
Support for multiple OAuth2 providers Automatic configuration and discovery of OAuth2 provider credentials Support for a variety of authentication mechanisms, including JWT tokens, cookies, and HTTP basic authentication Fine-grained access control through the use of role-based access control (RBAC) Support for custom headers and footers to customize the user interface Overall, OAuth2 Proxy is a powerful tool for securing web applications using OAuth2 providers. It simplifies the authentication and authorization process and makes it easy to manage access to your applications in a Kubernetes environment.
- geek-cookbook.funkypenguin.co.nz: Using OAuth2 proxy for Kubernetes Dashboard In this tutorial, you will learn how to set up OAuth2 Proxy to pass authentication headers to Kubernetes Dashboard, which doesn’t provide its authentication but instead relies on Kubernetes’ own RBAC auth
- imanishchaudhary.medium.com: Securing Kubernetes Dashboards: SSO Authentication and RBAC Implementation with Okta and OAuth2 Proxy
Alternatives
There are several alternatives to OAuth2 Proxy in Kubernetes, depending on your specific use case and requirements. Some popular options include:
Istio: Istio is a popular open-source service mesh that provides a variety of features, including secure authentication and authorization through its Istio Authentication feature. Istio allows you to define authentication policies for your services using a variety of authentication mechanisms, such as JWT, OAuth, and mTLS.
Keycloak: Keycloak is an open-source identity and access management solution that provides a variety of features, including authentication, authorization, and user management. Keycloak can be deployed on Kubernetes using its Helm chart and can be used to secure your Kubernetes applications using a variety of authentication mechanisms, such as OAuth2, OpenID Connect, and SAML.
Dex: Dex is an open-source identity provider that can be used to provide authentication and authorization for Kubernetes applications. Dex can be deployed on Kubernetes using its Helm chart and can be used to authenticate users using a variety of authentication mechanisms, such as LDAP, OAuth2, and OpenID Connect.
Traefik: Traefik is a popular open-source reverse proxy and load balancer that provides a variety of features, including secure authentication and authorization. Traefik can be used to secure your Kubernetes applications using a variety of authentication mechanisms, such as OAuth2, JWT, and basic authentication.
Ambassador: Ambassador is a popular open-source API Gateway that provides a variety of features, including secure authentication and authorization. Ambassador can be used to secure your Kubernetes applications using a variety of authentication mechanisms, such as OAuth2, JWT, and basic authentication.
Each of these alternatives provides different features and may be more suitable for different use cases. It’s important to evaluate each option based on your specific needs and requirements.
RBAC and Access Control
- Kubernetes does not have objects which represent normal user accounts. Normal users cannot be added to a cluster through an API call. So how do you create a user?
- Configure RBAC in Kubernetes Like a Boss 🌟 Learn how to configure RBAC in kubernetes. In this post, you will configure RBAC both with kubectl and yaml definitions.
- infracloud.io: How to setup Role based access (RBAC) to Kubernetes Cluster 🌟
- Kubernetes RBAC Permission Manager 🌟
- Krane 🌟 is a Kubernetes RBAC static analysis tool. It identifies potential security risks in K8s RBAC design and makes suggestions on how to mitigate them. Krane dashboard presents current RBAC security posture and lets you navigate through its definition.
- rbac.dev 🌟🌟🌟 advocacy site for Kubernetes RBAC. A site dedicated to good practices and tooling around Kubernetes RBAC. Both pull requests and issues are welcome.
- For recipes, tips and tricks around RBAC see recipes.rbac.dev 🌟
- github.com/clvx/k8s-rbac-model: Kubernetes RBAC Model This is a implementation of a RBAC model for a multi project multi tenant Kubernetes cluster.
- loft.sh: Kubernetes RBAC: Basics and Advanced Patterns
- marcusnoble.co.uk: Restricting cluster-admin Permissions Generally, operators of the cluster are assigned to the cluster-admin ClusterRole. This gives the user access and permission to do all operations on all resources in the cluster. But what if you need to block an action performed by cluster admins?
- medium.com/devops-mojo: Kubernetes — Role-Based Access Control (RBAC) Overview RBAC with Kubernetes — Role, ClusterRole, RoleBinding, and ClusterRoleBinding.
- loft-sh.medium.com: 10 Essentials for Kubernetes Access Control
- sumanthkumarc.medium.com: Kubernetes RBAC — Update default ClusterRoles without editing them
- faun.pub: Assign permissions to an user in Kubernetes. An overview of RBAC-based AuthZ in k8s 🌟
- anaisurl.com: RBAC Explained with Examples 🌟 Kubernetes RBAC tutorial with two examples, using ServiceAccounts and openssl to create separate contexts for users
- medium.com/@badawekoo: Using RBAC in Kubernetes for authorization-Complete Demo-Part 1
- thenewstack.io: Securing Access to Kubernetes Environments with Zero Trust
- learnk8s.io: Limiting access to Kubernetes resources with RBAC 🌟🌟🌟 What happens when you combine a Kubernetes RoleBinding to a ClusterRole? Are you even allowed? In this article, Yanan Zhao explores the K8s RBAC authorization model by rebuilding it from scratch.
- medium.com/@15daniel10: YOYO attack on a K8S cluster In addition to the performance degradation for the attacked service, the underlying idea behind the attack is to exploit the autoscaling mechanism in order to make the victim deploy excessive resources and pay for them while having as little cost footprint for the attacker as possible. In other words, the attacker harnesses the power of the cloud against the organization that uses it.
- dev.to: Binding AWS IAM roles to Kubernetes Service Account for on-prem clusters | Daniele Polencic 🌟 AWS IAM to Kubernetes service accounts integration, but for on-prem clusters (i.e. non EKS, just regular clusters). Process to grant permissions to Pods.
- learnk8s.io/rbac-kubernetes: Limiting access to Kubernetes resources with RBAC 🌟
- medium.com/@danielepolencic: How does RBAC work in kubernetes 🌟 A short and visual thread on how Kubernetes RBAC works in Kubernetes
- dominik-tornow.medium.com: Inside Kubernetes RBAC
- medium.com/@jtdv01: Kubernetes Authorization and Role Based Access Controls 🌟
- faun.pub: Give Users and Groups Access to Kubernetes Cluster Using RBAC Role-based access control (RBAC) is a way of granting users granular access to Kubernetes API resources. RBAC is a security design that limits access to Kubernetes resources based on the user’s role.
- medium.com/@danielepolencic: AWS IAM Roles for service accounts for on-prem clusters In this short tutorial, you will learn how to configure the IAM roles for Service Account for a bare-metal cluster using minikube as an example.
- medium.com/andcloudio: Setting up Authentication and RBAC Authorization in Kubernetes
- dev.to: Configure RBAC in Kubernetes Like a Boss You will configure RBAC both with kubectl and yaml definitions.
- raesene.github.io: Auditing RBAC - Redux The challenges of auditing Kubernetes authorization. Auditing Kubernetes authorization can be a bit of a tricky task. In this article, you will learn what techniques and tools you can use to identify, reassign and manage RBAC rules in your cluster.
- goteleport.com: A Simple Overview of Authentication Methods for Kubernetes Clusters
- medium.com/@mehmetodabashi: Authentication and Authorization in Kubernetes: Client Certificates and Role Based Access Control (RBAC) In this tutorial, you’ll learn how to authenticate and authorize a user to access Kubernetes Clusters with client certificates
- medium.com/@brunoolimpio: Kubernetes DeepDive — Parte 2 - Kubernetes RBAC and more… | Bruno Olimpio
- youtube: Kubernetes RBAC Explained | Anton Putra 🌟
Tools
- paralus.io 🌟 Zero trust Kubernetes with zero friction. - github.com/paralus/paralus Paralus is a free, open source tool that enables controlled, audited access to Kubernetes infrastructure. It comes with just-in-time service account creation and user-level credential management that integrates with your RBAC and SSO providers or Identity Providers (IdP) that support OIDC. Ships as a GUI, API, and CLI.
- github.com/ondat/trousseau Trousseau uses the Kubernetes KMS provider framework to provide an envelope encryption scheme to encrypt secrets on the fly before they reach etcd. The project is modular and you can plug your own KMS tool (e.g. Vault).
Kubernetes and LDAP
Admission Control
- blog.styra.com: Why RBAC is not enough for kubernetes security 🌟🌟
- medium: Single Sign-On in Kubernetes 🌟
- trstringer.com: Create a Basic Kubernetes Validating Webhook
- box/kube-exec-controller An admission controller service and kubectl plugin to handle container drift in K8s clusters
Kubernetes Security Best Practices
- Kubernetes Security 101: Risks and 29 Best Practices 🌟 Security Best Practices Across Build, Deploy, and Runtime Phases.
- Build Phase:
- Use minimal base images
- Don’t add unnecessary components
- Use up-to-date images only
- Use an image scanner to identify known vulnerabilities
- Integrate security into your CI/CD pipeline
- Label non-fixable vulnerabilities
- Deploy Phase:
- Use namespaces to isolate sensitive workloads
- Use Kubernetes network policies to control traffic between pods and clusters
- Prevent overly permissive access to secrets
- Assess the privileges used by containers
- Assess image provenance, including registries
- Extend your image scanning to deploy phase
- Use labels and annotations appropriately
- Enable Kubernetes role-based access control (RBAC)
- Runtime Phase:
- Leverage contextual information in Kubernetes
- Extend vulnerability scanning to running deployments
- Use Kubernetes built-in controls when available to tighten security
- Monitor network traffic to limit unnecessary or insecure communication
- Leverage process whitelisting
- Compare and analyze different runtime activity in pods of the same deployments
- If breached, scale suspicious pods to zero
- thenewstack.io: 6 Kubernetes Security Best Practices 🌟
- kodekloud.com: Kubernetes Security Best Practices
- armosec.io: Kubernetes Security Best Practices: Definitive Guide
- semaphoreci.com: Secure Your Kubernetes Deployments In this tutorial, we present three tools to validate and secure your Kubernetes deployments:
- Kubeval
- Kubeconform
- Kubescore
- engineering.dynatrace.com: Kubernetes Security Best Practices -Part 1: Role Based Access Control (RBAC)
- medium.com/dynatrace-engineering: Kubernetes Security Best Practices Part 2: Network Policies In this blog post, you’ll cover the following topics:
- What a NetworkPolicy is, and why do you need it
- How NetworkPolicies are structured
- Best practices for defining NetworkPolicies
- An example of defining NetworkPolicies
- blog.frankel.ch: Learning by auditing Kubernetes manifests In this article, you will learn about Kubernetes security and architecture by reviewing reports from Chekov — a tool designed to find misconfigurations before they’re deployed.
- spectrocloud.com: Kubernetes security best practices: 5 easy ways to cut risk
- medium.com/@cloud_tips: Kubernetes Security Best Practices
Kubernetes Authentication and Authorization
- kubernetes.io: Authenticating
- kubernetes.io: Access Clusters Using the Kubernetes API
- kubernetes.io: Accesing Clusters
- magalix.com: kubernetes authentication 🌟
- magalix.com: kubernetes authorization 🌟
- kubernetes login
- learnk8s.io: Authentication between microservices using Kubernetes identities 🌟
- gravitational.com: How to Set Up Kubernetes SSO with SAML
- lisowski0925.medium.com: Using Kubernetes Certificate Signing Requests and RBAC for User Authentication and Authorization
Kubernetes Authentication Methods
Kubernetes supports several authentication methods out-of-the-box, such as X.509 client certificates, static HTTP bearer tokens, and OpenID Connect.
X.509 client certificates
Static HTTP Bearer Tokens
- kubernetes.io: Access Clusters Using the Kubernetes API
- stackoverflow: Accessing the Kubernetes REST end points using bearer token
OpenID Connect
Implementing a custom Kubernetes authentication method
Pod Security Policies (SCCs - Security Context Constraints in OpenShift)
- Pod Security Policy (SCC in OpenShift) 🌟
- rancher.com: Enhancing Kubernetes Security with Pod Security Policies, Part 1
- developer.squareup.com: Kubernetes Pod Security Policies (PSP) an example with exception management
- itnext.io: Implementing a Secure-First Pod Security Policy Architecture
- Neon Mirrors: Kubernetes Policy Comparison: OPA/Gatekeeper vs Kyverno
- ibrahims.medium.com: Security Context — Kubernetes
Security Profiles Operator
- The Security Profiles Operator (SPO) is an out-of-tree Kubernetes enhancement to make the management of seccomp, SELinux and AppArmor profiles easier and more convenient.
- kubernetes-sigs/security-profiles-operator
- kubernetes.io: What’s new in Security Profiles Operator v0.4.0
EKS Security
- Security Group Rules EKS
- EC2 ENI and IP Limit
- Calico in EKS
- Amazon EKS Best Practices Guide for Security 🌟
- medium.com: Securing Kubernetes Dashboard on EKS with Pomerium
External Secrets Operator
- external-secrets.io 🌟 External Secrets Operator is a Kubernetes operator that integrates external secret management systems like AWS Secrets Manager, HashiCorp Vault, Google Secrets Manager, Azure Key Vault, IBM Cloud Secrets Manager, and many more. The operator reads information from external APIs and automatically injects the values into a Kubernetes Secret.
- mahira-technology.medium.com: Kubernetes Secrets Management: Level Up with External Secrets Operator Kubernetes has become a popular platform for deploying and managing containerized applications. As applications grow in complexity, managing secrets such as API keys, passwords, and certificates becomes increasingly important. While Kubernetes provides a built-in Secrets resource, it has limitations when it comes to managing secrets across multiple clusters or integrating with external secret management systems. This is where the External Secrets Operator (ESO) comes into play. ESO is an open-source Kubernetes operator that allows you to manage secrets from external secret management systems and synchronize them as Kubernetes Secrets.
- faun.pub: External Secret Operator on AKS (with Terraform) for Azure Key Vault Integration (with Workload Identity)
CVE
- hackerone.com: Authenticated kubernetes principal with restricted permissions can retrieve ingress-nginx serviceaccount token and secrets across all namespaces
- blog.lightspin.io: NGINX Custom Snippets CVE-2021-25742
Official Kubernetes CVE Feed
- kubernetes.io: Official CVE Feed 🌟
- kubernetes.io: Announcing the Auto-refreshing Official Kubernetes CVE Feed
Videos
Click to expand!
Tweets
Click to expand!
Kubernetes base64 encodes secrets because that makes arbitrary data play nice with JSON. It had nothing to do with the security model (or lack thereof). It did not occur to us at the time that people could mistake base64 for some form of encryption.
— Daniel Smith (@originalavalamp) July 4, 2021
#OAuth has 4 Flows for retrieving an Access Token.
— Rohit (@sec_r0) January 8, 2021
If you have worked with it, you know how difficult is it to remember what is what.
A Zine says a lot, seriously a lot. Check this out.
Idea credits @b0rk #IAM #security #infosec #webdev #web #webcomic #webcomics
RT if useful pic.twitter.com/fbrls0V08K
Kubernetes security best practices in short -
— Rakesh Jain (@devops_tech) October 9, 2021
A Thread 👇 pic.twitter.com/kehRjXuiEw
Kubernetes security thing: Always be careful of what you are letting your users choose for usernames. If somone has a username of system:kube-controller-manager on an external Identity system, Kubernetes will quite happily give them the rights of the controller manager :)
— Rory McCune (@raesene) November 1, 2021